Threat Update
The BlackByte Ransomware-as-a-Service group is quickly gaining traction by infecting and cryptolocking multiple companies. Reports regarding this ransomware in the wild have existed since July 2021. In response, the FBI and USSS (United States Secret Service) have issued a joint threat advisory. FinGarde recommends that companies keep their machines patched and protected with endpoint protection solutions in order to mitigate the risk of this threat.
Technical Detail & Additional Information
WHAT IS THE THREAT?
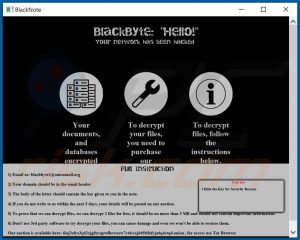
The BlackByte ransomware is a Ransomware-as-a-Service strain used by threat actors to hold a company’s assets and data at ransom. Malicious users have been exploiting patched vulnerabilities in order to gain an initial foothold on networks, and then deploying ransomware to assets that they have access to. There have been multiple strains caught in the wild, including ones that download a .png file from malicious IP addresses. However, there are also strains of this ransomware that encrypt files without communicating with external hosts.
WHY IS IT NOTEWORTHY?
This spike in activity is especially noteworthy due to how prevalent these attacks are, and the companies the ransomware has impacted. Most recently, threat actors were able to beach the San Francisco 49ers football team’s IT infrastructure. Threat actors then leaked data onto a public blog for anyone to view. This is a clear example of why it is important to keep servers and machines up to date, as Microsoft Exchange compromises are the primary reason for compromise.
WHAT IS THE EXPOSURE OR RISK?
Companies should be extremely vigilant and worried about this attack as the threat actors have been known to leak data once obtained. Though a free decryptor tool exists online for this ransomware strain, the malicious users may change the encryption key or leak any data obtained from a company once compromised. The company then faces legal ramifications as well as the workload in order to remediate the attack.
WHAT ARE THE RECOMMENDATIONS?
FinGarde recommends the following actions to limit the impact of a VoIP DDoS attack:
- Keep your systems patched and up to date to prevent initial compromise from threat actors.
- Block the known malicious IPs on your firewalls to prevent communication to the threat actor network: 185.93.6.31 and 45.9.148.114
- Maintain a strong password policy in order to prevent passwords from being compromised.
- Ensure users are wary of phishing and spam attacks where threat actors may compromise one user’s machine which then compromises others.
- Review the joint threat advisory from the FBI and USSS in order to block and mitigate the IOCs: https://www.ic3.gov/Media/News/2022/220211.pdf
REFERENCES
For more in-depth information about the recommendations, please visit the following links:
- https://www.cisa.gov/uscert/ncas/current-activity/2022/02/15/fbi-and-usss-release-advisory-blackbyte-ransomware
- https://www.ic3.gov/Media/News/2022/220211.pdf
- https://www.bleepingcomputer.com/news/security/fbi-blackbyte-ransomware-breached-us-critical-infrastructure/
- https://securityaffairs.co/wordpress/127961/cyber-crime/blackbyte-ransomware-hit-san-francisco-49ers.html
If you have any questions, please contact us.
